Recently I started taking a basic course in Computer-Aided Design (CAD) at George Brown College – mostly for interest’s sake, although it’s partly because my day job at CBC is exposing me more and more to the engineering side of things, and I imagine it’ll only be a matter of time before I’ll have to start looking at technical drawings. The instructor recommended on day one that we all purchase USB memory keys to save our work, because there are no personal home directories on the George Brown network. Thus begins the sorry tale of how I managed to get a virus on my CBC-issued Windows laptop – thanks Microsoft! Continue reading
Windows
There are 12 posts filed in Windows (this is page 1 of 2).
exporting IIS SSL certificates for use in Apache
I didn’t think you could do this, but it is possible to export SSL certificates creating under a Windows IIS environment for use in Apache. Here’s how to do it:
- On the Windows box, fire up Microsoft Management Console (mmc.exe) and add the Certificates snap-in. Choose Computer Account and then Local Computer.
- Find the certificate that you want to export and choose All Tasks > Export. Follow the Export wizard and make sure you export the private key too. You’ll be asked for a passphrase to use to encrypt the key.
- Take the PFX-format file that was created by the wizard and copy it to your UNIX machine.
- Use OpenSSL to convert the PFX file into a PKCS12 format:
$ openssl pkcs12 -in whatever.pfx -out pfxoutput.txt
- The PKCS12 output file is basically a concatenation of the private key and the certificate, so use vi to slice it up into two files, a .crt for the cert and a .key for the private key.
- If you want to remove the passphrase from the key (highly recommended in a production environment where Apache must start up unattended) then just run:
$ openssl rsa -in encrypted.key -out unencrypted.key
That’s it! You can now use the key and cert in your Apache config files.
authenticating Apache against Windows 2003 Active Directory
Devlin’s rebuilding its intranet and moving away from the old Lotus Domino-based directory service. One of the developers on the intranet project asked me if he could authenticate employees against Active Directory instead. He’ll be using the MODx CMS, and would like to authenticate using mod_auth_ldap.
We’ve done this before to authenticate Subversion SCM users, but just as a test. This time I decided to try and create a user in Active Directory that would be used solely to bind to LDAP when doing lookups. I called this user “LDAP User”.
Making this work required a lot of trial and error, and I still haven’t managed to figure out a few things (see below). The first problem I had was that I was confused as to what the CN actually is for this particular user: it’s going to be cn=LDAP User, cn=Users, dc=devlin, dc=ca rather than cn=ldapuser, cn=Users, dc=devlin, dc=ca. ldapuser is just the login ID of the account rather than the actual CN.
The other thing I did wrong is that I put quotes around the Require statement, so rather than having
Require group “cn=Devlin Employees,cn=Users,dc=devlin,dc=ca”
the correct syntax is just
Require group cn=Devlin Employees,cn=Users,dc=devlin,dc=ca
A few things are still broken:
- I can’t figure out why LDAPS isn’t working. Doing searches from the command line using ldapsearch over SSL work fine, but the configuration of LDAP-SSL within Apache seems to be really tricky. I already have the directives
LDAPTrustedCA certs/sf_issuing.crt LDAPTrustedCAType BASE64_FILEin the configuration file, and Apache does say [notice] LDAP: SSL support available, but any attempt to actually use it gives an
[LDAP: ldap_simple_bind_s() failed][Can't contact LDAP server]
error.
- I’m not particularly impressed that AuthLDAPBindPassword is stored in cleartext in the configuration file, but there doesn’t seem to be a way of hashing it or otherwise concealing it.
- I haven’t figured out how to enable LDAPS on Domain Controllers that aren’t already HTTPS-enabled, so for now I’m not authenticating against them.
I should just get my parents a Mac Mini
I’ve been preparing an old IBM PC 300PL for my parents to replace their generic clone that died (RIP the machine formerly known as exodus.dreaming.org). They’re familiar with Windows, so I installed Windows 2000 Professional, ran Windows Update to download all the latest patches, and installed ClamWin as a virus scanner, and ZoneAlarm as a firewall. Fortunately they don’t have Internet access yet, but I worry about them clicking on some malware link and having some nasty spyware/trojan/virus take over their machine.
Despite all this, somewhere along the line I picked up some nasty trojan. This particular strain, TROJ_CONHOOK.AE, attached itself to WINLOGON.EXE so even booting in Safe Mode wouldn’t get rid of it. It saved itself as a randomly-named DLL (in my case, C:WINNTSYSTEM32pmnmlml.dll) and added itself as an AutoRun all over the place, a fact I was able to ascertain by using SysInternals‘ excellent Autoruns utility. Using another SysInternals utility, ProcessExplorer, I was also able to see that it was causing WINLOGON.EXE to run some routine inside the DLL file every second!
Call me a skeptic but I was still not totally convinced that pmnmlml.dll was not some legitimate Windows DLL. After all, just open your C:WINNTSYSTEM32 and half the stuff in there looks like a virus. (Quick: is dcomcnfg.exe a virus? How about dcomcfg.exe?) So I decided to copy the DLL to my Linux workstation and run strings(1) on it. Sure enough, the following text string was enough confirmation for me to see that it was a trojan:
http://82.98.235.63/cgi-bin/check/autoaff3
So I followed the procedure on Trend Micro’s site for getting rid of it — namely, booting off the Windows 2000 Professional CD and running the recovery console, then deleting the DLL.
Let’s step back for a second here. I am a professional system administrator, and my parents are not. How can I expect them to surf the Internet safely and not suck down one or more of these nasty trojans? Next thing I know, I’ll be getting a call from their ISP telling me that their little IBM is sending out 10,000 spams a minute, or is the control point for some DoS botnet.
I’m leaning more and more towards just getting them a Macintosh. I just have to convince them to part with their beloved Windows.
(By the way, dcomcnfg.exe is legitimate, while dcomcfg.exe is not. But how would one ever tell?
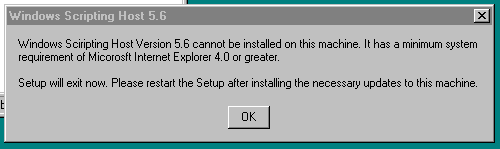
those wily Micorosft Sciript writers (sic)
I don’t like M$ Windows, but…
… since I have to grudgingly administer some Windows boxes, I’m finding this site pretty valuable. For example, someone asked me this morning if we have inbound and outbound message size limits in Exchange. This article explains how to find that information!
bad ideas in usability
At my new company I unfortunately have to deal with Active Directory. I understand that AD is supposed to be the authoritative source for any information about users, groups, computers, and so on, but does the interface have to be so crammed with junk?
This has got to be the worst interface I’ve ever seen (Lotus Notes aside, but I’ve never had to administer Notes). It’s not clear where to find anything! Not only is the interface kludgy (multiple rows of tabs?) but the tab labels are totally non-intuitive. Why are there at least four tabs pertaining to e-mail (Microsoft Exchange)? What the heck is the Member Of tab for, and how does that differ from what I might find under Account?
I can’t imagine trying to administer hundreds of users with this kludgy tool. Thank God our company is only < 50 people.
tape hardware, part two
While on the topic of tape hardware and backups… never mind my little DLT7000 drive at home. How do you back up a 4TB Titan NAS?
We bought one of these servers at work last year; we’re finally getting around to using it for something. Our current challenge is trying to figure out how to back up a 1TB Interwoven content store (we’ve just bought almost the entire product line from Interwoven) without IT screaming at us for taking up their entire tape rotation schedule. This is on top of having to back up a large MediaBin store as well.
I’ll be happy when the Titan is actually up and running, though. We’ve been having some problems getting the CIFS partitions running, because the Titan really needs an Active Directory server in order to enforce permissions, and all we have is a Windows NT 4 domain controller (think again about hacking it; it’s on an internal network). The problem is that we never originally intended the Titan to be used for Windows shares; the unit was purchased long before we decided to go with Interwoven on Windows entirely.
Interesting technical challenges abound…
The Windows Crash Gallery
If you want a good laugh, head on over to windowscrash.com. There’s nothing like a whole gallery of BSODs showing up on public billboards, airport screens and payphones to demonstrate just how unstable and unusable Windows is.
There’s also a fantastic collection of meaningless and just downright hilarious Windows error messages there. My favourite is this one entitled Mouse. This one comes a close second though.
*LET* the Lawsuits Fly.
Wow. It’s been a while since I last wrote. Happy Hallowe’en, by the way.
I now work for CBC.ca in the New Media Production & Operations department as a software developer. Primarily this involves Java development, but I also do a bit of Perl (as much as I hate to). I also weigh in on system administration matters quite a bit, since I think of myself as a half-time sysadmin, half-time programmer.
I just had to respond to this slightly brain-damaged article which appeared in eWeek recently. Now I know eWeek is one of these magazines for PHBs but I still like to flip through it (very briefly) to see what the PHBs are being told these days, and how I can counteract that. So this article — if you go and read it — basically says well, Microsoft has to make "Longhorn" really secure, and improve their security in general, or else legislatures will impose security warranties upon software developers, and this will impact all developers and not just Microsoft.
My reaction — as both a sysadmin and a developer — is: so what? Isn’t that a good thing? I’ve often railed about the fact that software is but one of the few industries where you can sell an expensive product to someone and not be held to any legal liability whatsoever. No warranty to speak of beyond the value of the actual compact disc that the software arrived on. In my mind, this is a bad thing. So when Brian Livingston says something like
Such an earthquake could emerge not just from legislatures but also from courts. All it would take would be a precedent-setting ruling that the “we’re-not-liable” language that’s commonplace in shrink-wrap licenses is “unconscionable and unenforceable.” The lawsuits would fly.
I think he’s bang on — but the lawsuits should fly, in fact, if the software is defective. This would certainly stop not only Microsoft from shipping poorly-tested products, but all software vendors.
On a lighter note — check this out. If you work for Allstate, you can submit your resignation online. No word on whether a security guard will be e-mailed to you to escort you out of the building, too. (Speaking of which — someone at work was joking about dressing up for Hallowe’en as a manager who was unceremoniously sacked some time ago. “I’ll just dress up two mannequins in security guard uniforms, put one under each arm, and I’ll be [name removed] being escorted out of the building!”)